Wikipedia defines Baby New Year as a “male baby wearing nothing more than a diaper, a top hat and a sash across his torso that shows the year he is representing. Sometimes he is holding an hourglass or is otherwise associated with one”.
Not too ominous at face value but this icon represents the anticipation, excitement, and uncertainty everyone feels in facing a new era. On the eve for 2010, the likely evolutions in Information Security (those foreseen and those yet unimagined) are certain to bring out the same feelings in CSO’s, CISO’s, CIO’s, CEO’s across the public and private sector.
Step 1: Learning from the past attacks
"Among all forms of mistake, prophecy is the most gratuitous.” - George Eliot
What was expected?
- Early predictions this decade anticipated that information security would be much better, more efficient, less complicated, with fewer attacks.
- Popular thinking was that vulnerabilities would flatten/decline, and so would breaches.
- Applications were expected to get simplified, smaller, less interdependent and less extensible
- Some even suggest that by 2010, a security Martin Luther would lead us through a class-action lawsuit that sparks a full-blown security reformation.
- In 1991, D. James Bidzos, then president of RSA created the buzz phrase “digital Pearl Harbor”; referring to a global InfoSec attack compounded by disrupted backup systems and leading to cascading failures and worldwide panic where the origin is later pinpointed to an avoidable vulnerability.
- Viruses and data breaches were seen as mischievous acts of disruptive individuals rather, not criminal enterprises.
- PKI was seen as the imminent solution to all authentication problems
- Reformers such as SEI’s Watts Humphrey, proposed solutions to software vulnerabilities through formalized software engineering best practices and requiring professional licensing, as within the medical field, to minimize threats by heightening quality and consistency.
What wasn't expect?
- Hoaxes - For example, the Baby New Year Hoax of 2007 claimed a Baby New Year Virus had infected up to 42 million computers worldwide.
- Complexity - Instead of being simplified applications became more complicated, architectures more sophisticated through SOA, virtualization, SaaS, etc.
- Out Sourcing - Rather than becoming a highly regulated, licensed profession software development moved to an out sourcing model where vendors and customers build solutions through composite teams world wide
- Abstraction - Information Security moved to an abstraction model with shared/standard components across applications for authentication, authorization, provisioning, roles management, etc.
- Protocol flaws- For example, researcher Marsh Ray of PhoneFactor discovered a hole within SSL/TLS that allowed man-in-the-middle attacks.
- Security as a Facade – For example, Security2010 offering dummy security cameras and solar powered dummy security cameras
- Social Networking – 10 years ago we struggled with AOL IM, Yahoo Webmail, and peer-to-peer networks like Napster and focused on server port 80; but by the end of the decade, the top concerns were Facebook, Twitter, and other Web 2.0 applications.
- Worms – Unlike Oscar the Grouch friend Slimey, the 2005 Samy worm on MySpace or Facebook’s Koobface, demonstrated the risks in opening the web to malware contributions from users, innocent or malicious.
- Get Shorty - Twitter fans love of mini-URL’s lead to vulnerabilities of their own
- Mafiaboy to Organized Crime – The Feb 2000 Denial of Service attack from the Canadian teenage named Mafiaboy temporarily brought down sites including CNN, Dell, eBay, and Yahoo but by the close of the decade attacks were lead by well organized and funded criminals to produce data breaches at Dave & Busters, Hannaford Brothers, Heartland Payment Systems, and TJX and Iraq Shia fighters hijacking the security camera’s in drone airplanes
- Gone Phishing – Clever con artists leveraging fast flux to rapidly switch domains locations and sites that felt like known banking sites successfully extracted PII from users trying to log-in, update, or review their accounts.
Step 2: Anticipating future threats
“Never assume the obvious is true.” - William Safire
What can we foresee now?
- Jail Bait – Apple’s restrictive policies on “approving” applications and limiting user control of the device has lead to a large & growing sub-culture of “jailbroken” phones. While this gives the user more access it opens the device to vulnerabilities. Conversely security vendors like Symantec, McAfee, Sophos, etc. cannot develop antivirus applications for the iPhone as Apple blocks necessary low-level access to the device.
- Rock’m Sock’m Androids - Google's Android is a natural attack for 2010, as Google is more open in allowing applications, but this is open to abuse by seemingly desirable applications functioning as malware.
- Hey! You! Get off of my cloud – Cyber-criminals combining stolen credit cards and hosting cloud services like Amazon’s EC2 have already started to use the new platform for Bots-as-a-Service or Malware-as-a-Service. Not to mention the legal liability facing cloud services around protected data from PII to pornography being stored on their servers unbenounced to them.
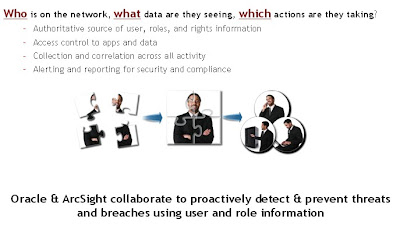
- It’s getting blurry - As public and private organizations extend their use of smartphones, web 2.0, and social media to interact with clients, employees, and contractors, they blur the perimeters of the network. Organizations will need to shift the focus towards data protection beyond network/infrastructure security as the question shifts from “Who has access to what?” to “What are they doing with it?”
- MyCloud.gov - Government agencies are increasingly moving data and services of low or moderate risk to cloud services to attain cost savings, such as Nasa’s Nebula http://www.cloudbook.net/nebula-gov or from the Pentagon http://www.networkworld.com/news/2009/100509-pentagon-cloud-computing.html?page=2
- Enough is Enough – As with the recent bombing attempt, the continuous evolution towards heightened security at airports and long, uncomfortable security screenings for most passengers will likely lead to biometrics finally making it to prime time. Consumers will be willing to compromise privacy and bear the cost to simplify their life with everything from air travel to eliminating the 100+ passwords they have to remember or keep in a file on their computer or sitting on the desk.
“No question is so difficult to answer as that to which the answer is obvious.” - George Bernard Shaw
What can’t we anticipate?
- Greatest Thing Since Sliced Bread – As we have seen throughout the evolution of enterprise software, there seems to be a never ending flow of revolutionary architectures changing how we build products, deploy solution, and conduct business. This includes CORBA, P2P, SOA, SaaS, Virtualization, and Cloud Services just to name a few. As each new platform emerges there will be new vulnerabilities associated with them.
- What’s Old is New Again – Appliances keep coming back as vendors like Intel and AMD seek to drive high-use functions into the chip set and organizations look to reduce the cost and risk associated with major deployments through the use of packaged solutions. However each new wave of appliances has its own associated risks.
- The Perfect storm – Who knows, perhaps the combination of social networking, smart phones, and cloud services will lead to the “digital Pearl Harbor” that was predicted in 1991