After "Who has access to what?” the question is “What are they doing with it?”
Information security has followed a similar path of information technology. First it was about storing and organizing information in databases and securing that information. Then as applications and middleware evolved to deliver that information and application entitlements to users, Identity and Access management suites developed to securily enable access to them.
But once information and entitlements are in the hands of users it is open for misuse. There are many examples of this:
- Accidentally emailing confidential information about M&A to the wrong internal user with the same name like John.Waters@xyzcorp.com instead of Jon.Waters@xyzcorp.com.
- Copying sensitive financial or personal information out of a protected application into a file and posting it on an open file share or SharePoint portal
- Sales person leaving the company who emails a list of accounts and contacts to themselves before going to work for a competitor.
- NT Admin who misues the shared account because they know they are 1 of 30 people with the password and nobody knows who did what with it.
- Former employees hacking into a company database because the password never changes as it is hard coded into applications.

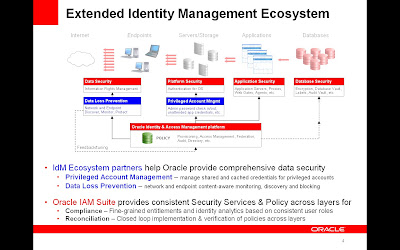
The list of potential risks/attacks goes on and on. To help customers identify these and address them, Oracle has once again expanded the Extended Identity Management Ecosystem to include:
- Privileged Account Management (PAM) – manage shared and cached credentials for privileged accounts
- Data Loss Prevention (DLP) – network and endpoint content-aware monitoring, discovery and blocking
Which is complimented by Oracle IAM solutions that provide consistent Security Services & Policy across layers for
- Compliance – Fine-grained entitlements and identity analytics based on consistent user roles
- Reconciliation – Closed loop implementation & verification of policies across layers
Our DLP partners (including McAfee, Symantec, & ControlGuard ) integrate with Oracle IRM to:
- Discover, classify, quarantine and seal (IRM-encrypt)
- Intercept file copies to removable media, classify, quarantine, seal (IRM-encrypt) & release
DLP integration with Oracle IAM will enable :
- DLP policies via OID or OVD group membership
- Provision/de-provision DLP policies via OIM (groups)
- Feedback/tuning of IAM
Similiarly Oracle PAM partners including Cloakware, Cyber-Ark, Liebsoft, and OpenTrust (formerly Symark) , deliver integrations that allows customers to:
- Leverage OID/OVD as identity/credential store
- PAM policies via OID/OVD groups
- Provision/de-provision policies via OIM (groups)
- Leverage Oracle database as secure policy store
- Secure caching of credentials for unattended application restarts
To learn more about these partners please visit their page on OPN or click on their name above to reach their website directly.
{NOTE: Please click on the above images to see the slides in full size for reading the details}